域外对域内的信息收集
很多时候为了避免在目标机器产生太大的动静,或者被AV检测到,经常通过socks代理在本地进行信息收集,但会产生大量的socks流量,容易被edr检测到。
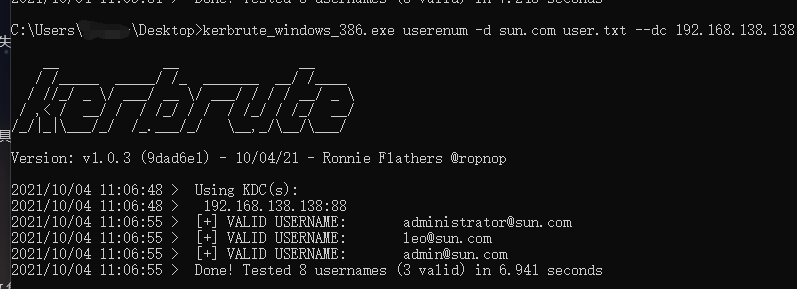
0x01 通过 kerbrute 枚举
下载地址:https://github.com/ropnop/kerbrute
原理:
通过模拟 AS_REQ 向 KDC 请求,如果 KDC 返回的是 KRB5KDC_ERR_C_PRINCIPAL_UNKNOWN 错误的话, 则说明该域⽤户不存在,如果 KDC 返回并提示 KRB5KDC_ERR_PREAUTH_REQUIRED (预身份验证),那么就说明该域⽤户是存在的
主要利用了 Kerberos 协议的预身份验证,预身份验证指的是 client 在发出票证之前已通过 KDC 的身份验证。
kerbrute的语法
1 | kerbrute.exe userenum -d 域名 字典.txt --dc 域控IP |
0x02 ADfind 搜集域内各类信息
下载地址:https://www.softpedia.com/get/Programming/Other-Programming-Files/AdFind.shtml
各种cs插件已经集成了此工具,z1等等。当然已经被AV杀烂了
使用方法:
1 | adfind.exe -help |
1 | AdFind V01.52.00cpp Joe Richards (support@joeware.net) January 2020 |
以下靶场使用的是 saulGoodman 师傅搭建的靶场,在操作过程中可能会因为靶场问题出现一点意外情况,本文仅展示方法。
这里获取到了 web-2012 机器的控制权限,并成功提权抓到了密码,接下来就通过抓到的⽤户去对域内进⾏枚举信息搜集。
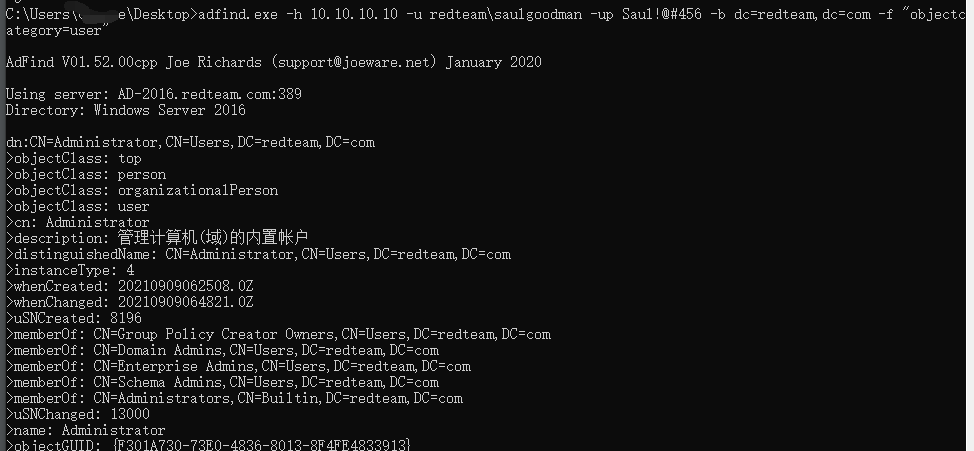
获取域内用户列表信息
1 | adfind.exe -h 10.10.10.10 -u redteam\saulgoodman -up Saul!@#456 -b dc=redteam,dc=com -f "objectcategory=user" |
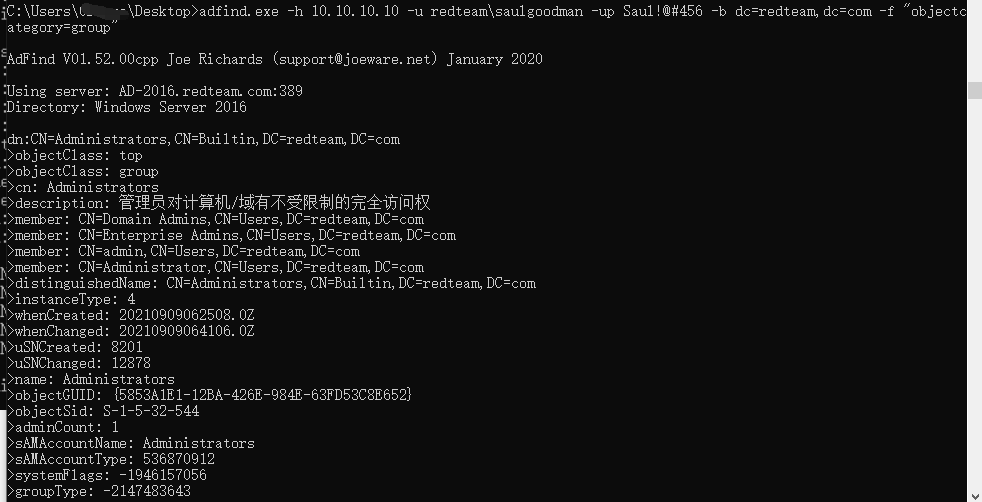
查询组信息
1 | adfind.exe -h 10.10.10.10 -u redteam\saulgoodman -up Saul!@#456 -b dc=redteam,dc=com -f "objectcategory=group" |
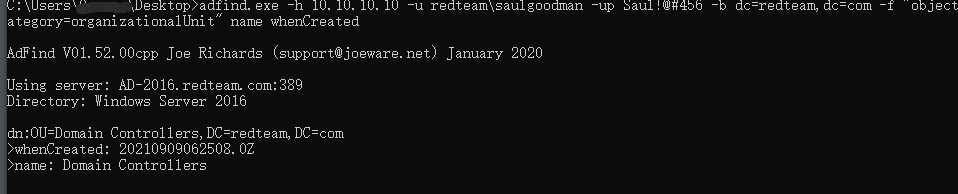
获取完整OU信息
1 | adfind.exe -h 10.10.10.10 -u redteam\saulgoodman -up Saul!@#456 -default -f |
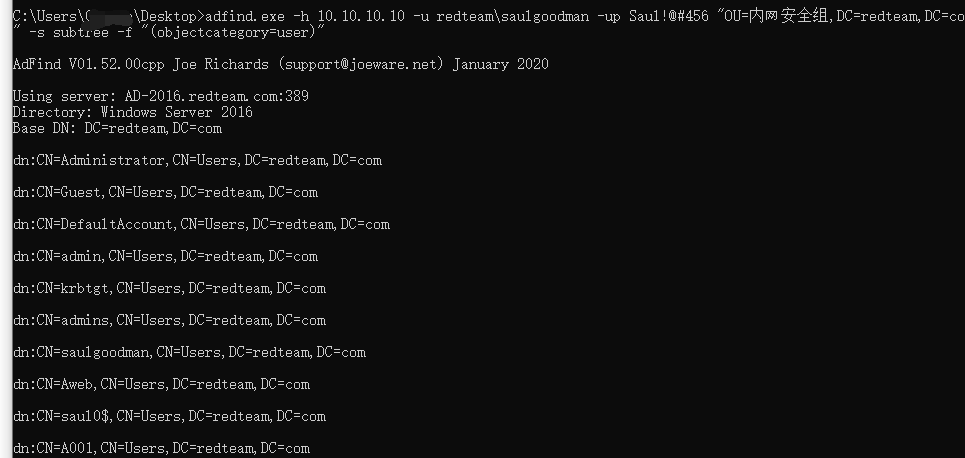
获取指定 OU 下的⽤户信息
1 | adfind.exe -h 10.10.10.10 -u redteam\saulgoodman -up Saul!@#456 "OU=内⽹安全组,DC=redteam,DC=com" -s subtree -f "(objectcategory=user)" |
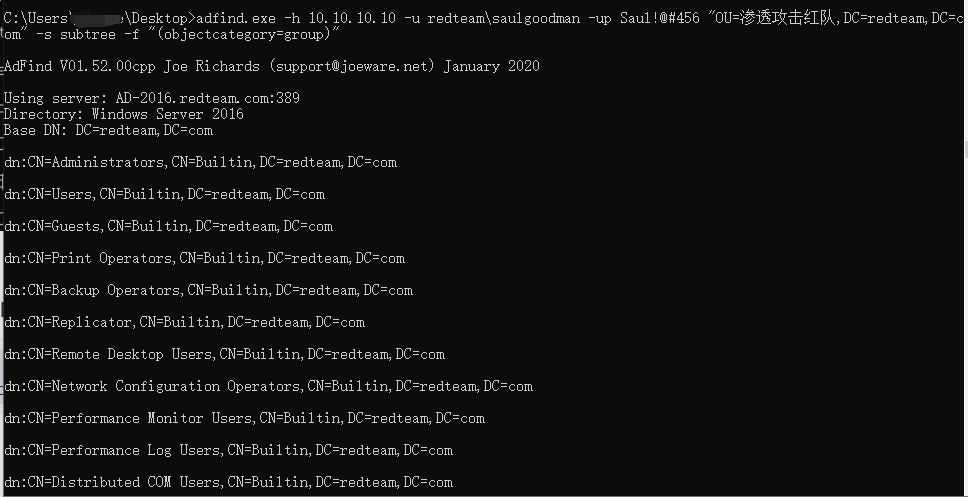
获取指定OU下的用户组信息
1 | adfind.exe -h 10.10.10.10 -u redteam\saulgoodman -up Saul!@#456 "OU=渗透攻击红队,DC=redteam,DC=com" -s subtree -f "(objectcategory=group)" |
获取指定OU下的机器名信息
1 | adfind.exe -h 10.10.10.10 -u redteam\saulgoodman -up Saul!@#456 "OU=内网安全组,DC=redteam,DC=com" -s subtree -f "(objectcategory=computer)" |
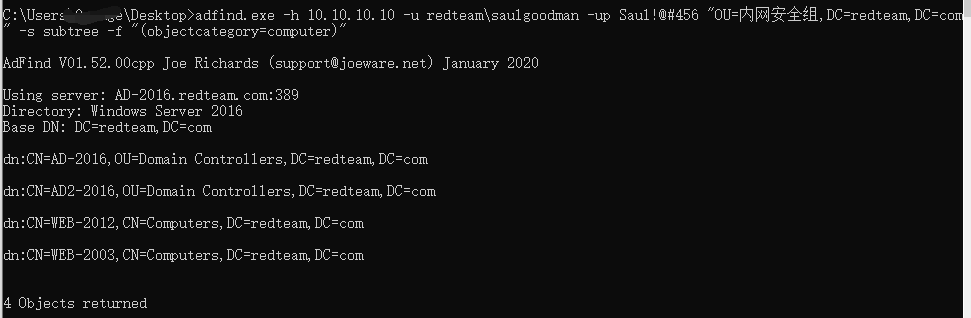
获取完整机器列表信息
1 | adfind.exe -h 10.10.10.10 -u redteam\saulgoodman -up Saul!@#456 -b dc=redteam,dc=com -f "objectcategory=computer" |
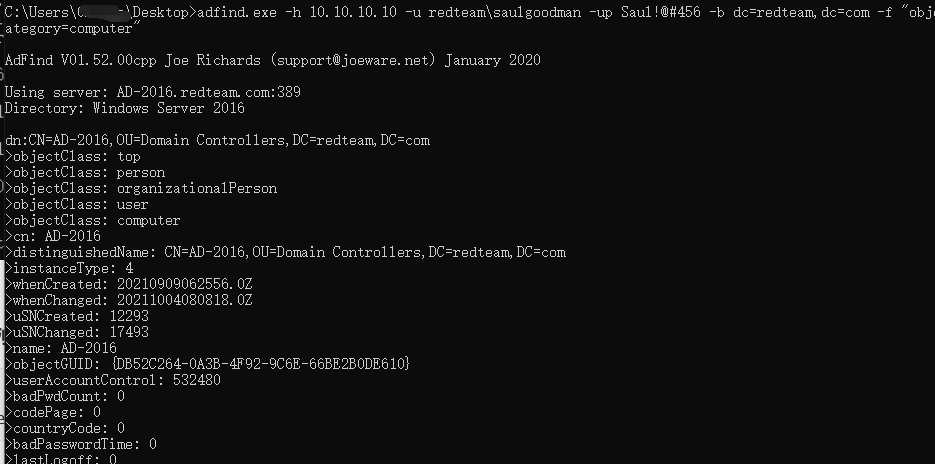
查询域内非约束委派(机器账户)
1 | adfind.exe -h 10.10.10.10 -u redteam\saulgoodman -up Saul!@#456 -b "DC=redteam,DC=com" -f "(&(samAccountType=805306369) (userAccountControl:1.2.840.113556.1.4.803:=524288))" cn distinguishedName |
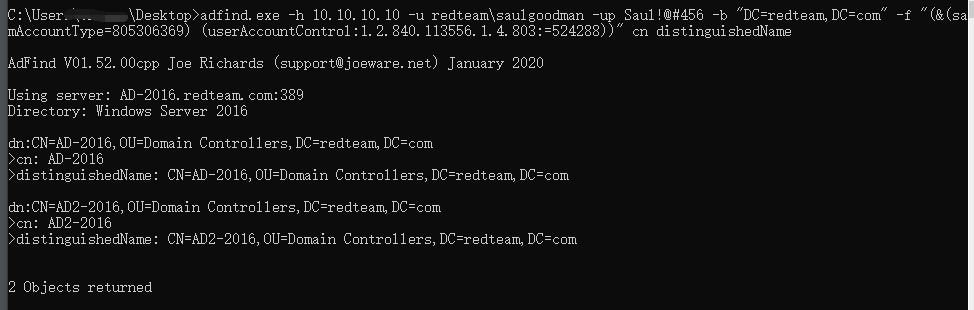
查询域内非约束委派(服务账户)
1 | adfind.exe -h 10.10.10.10 -u redteam\saulgoodman -up Saul!@#456 -b "DC=redteam,DC=com" -f "(&(samAccountType=805306368) (userAccountControl:1.2.840.113556.1.4.803:=524288))" cn distinguishedName |
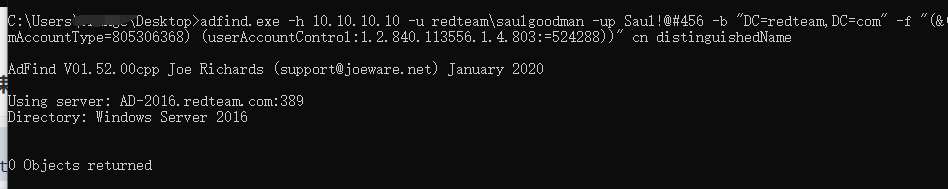
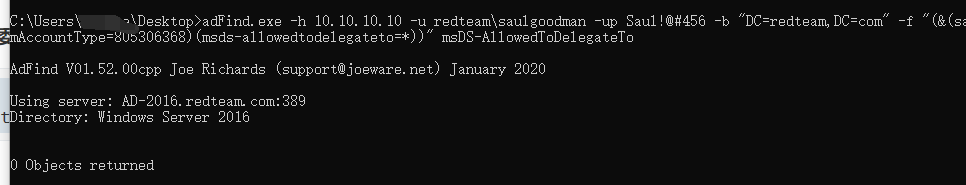
查询域内约束委派(机器账户)
1 | adFind.exe -h 10.10.10.10 -u redteam\saulgoodman -up Saul!@#456 -b "DC=redteam,DC=com" -f "(&(samAccountType=805306368)(msds-allowedtodelegateto=*))" msDS-AllowedToDelegateTo |
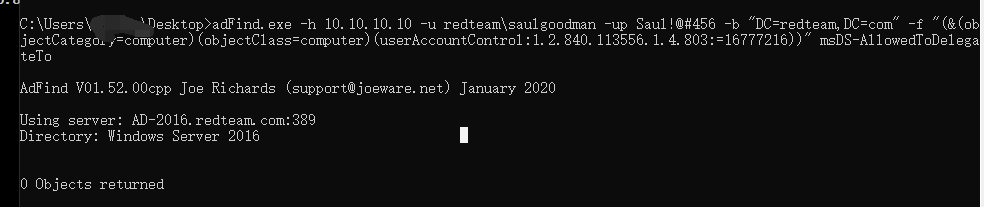
查询域内约束委派(服务账户)
1 | adFind.exe -h 10.10.10.10 -u redteam\saulgoodman -up Saul!@#456 -b "DC=redteam,DC=com" -f "(&(objectCategory=computer)(objectClass=computer)(userAccountControl:1.2.840.113556.1.4.803:=16777216))" msDS-AllowedToDelegateTo |
总结
Adfind 这款工具主要是基于 LDAP协议 来进行信息收集,帮助更快认识域的组成结构。
几个常见的 LDAP 端口
1 | 389/LDAP |
AD 与 LDAP 的关系:LDAP 是⼀种⽤来访问 AD 数据库的⽬录服务协议,AD DS 会通过 LDAP 名称路径来表示对象在 AD 数据库中的位置,以便⽤它来访问 AD 数据库内的对象。LDAP 的名称路径包括有 DN、RDN。
通过 Ad Explorer 图形化查看域内各类信息
AD Explorer是独⽴的可执⾏⽂件,⽆需安装就可以使⽤。使⽤前⾸先需要⼀个域帐户(任何⼀个域帐户都可以 ),可以利⽤该账户与域控制器通信并⽤它枚举域。它能够列出域组织架构,⽤户帐户,计算机帐户等。它可以 帮助你寻找特权⽤户和数据库服务器等敏感⽬标。
Ad Explorer 下载地址:http://live.sysinternals.com/
在拥有域成员账号和域控IP的情况下,可以查看域内信息
总结
核心就是在拿下一台域内主机后,开socks代理,主要目的是为了规避杀软,同样的可以使用 nmap、fscan、nbtscan 等端口扫描工具来进行信息收集,结合一下,根据域内成员结构、端口开放服务、各个网段等各种突破口 制定详细的进攻计划。
Peace